Understanding Metadata in Digital Forensics: HTML vs. EXIF
Introduction
In the realm of digital forensics and legal investigations, understanding the nuances of metadata is crucial. Metadata, known as "data about data," provides essential context and information about digital files. This blog post aims to clarify the differences between HTML metadata and EXIF data, discuss their implications in legal contexts, and offer practical advice for investigators. This topic was suggested by Drew Sustaita, whose insights have been invaluable in shaping this discussion.
HTML Metadata
HTML metadata is embedded within the HTML code of a web page and is primarily used for web page presentation and interaction. It includes elements such as:
- Page Title: The name displayed on the browser tab.
- Meta Tags: Information like description, keywords, and author, included in
<meta>tags. - Open Graph Data: Used for rich previews on platforms like Facebook or LinkedIn.
- Server-Side Data: Timestamps for when the post was created, uploaded, or last edited.
This type of metadata is generated by the platform's system, which does not originate from the uploaded file itself. It is crucial for investigators to understand that HTML metadata reflects server-side data, which is often captured during social media scraping [1].
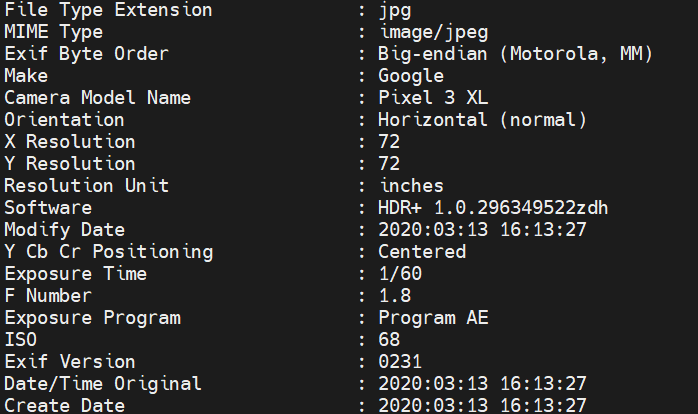
EXIF Data (Exchangeable Image File Format)
EXIF metadata is embedded directly in image files by the recording device, such as a camera or smartphone. It includes:
- Device Information: Camera make and model, lens details.
- Capture Date/Time: The date and time the image was taken.
- GPS Coordinates: The location where the image was captured (if enabled).
- Software Information: Details on edits made using specific tools [11].
While EXIF data can provide valuable evidence in investigations, investigators should be aware of its limitations. Camera settings might have incorrect time zones, GPS data can be imprecise in urban areas, and some image editing software can strip or modify EXIF data [11].
Video Metadata
While commonly confused with EXIF data, videos actually use different metadata formats. Common video metadata standards include:
- XMP (Extensible Metadata Platform): Adobe's metadata format that can be used across various file types
- QuickTime metadata: Used in .MOV and some .MP4 files
- MXF (Material Exchange Format): Common in professional video workflows
- ID3: Used primarily with MP4 video files
Like EXIF data for images, video metadata can include:
- Creation date and time
- Device information
- GPS coordinates (if enabled)
- Technical specifications (codec, resolution, frame rate)
- Copyright and authorship information
Both EXIF data and video metadata reside client-side, meaning they are attached to the original files. However, when media is uploaded to social media platforms, this metadata is often stripped to save space and protect user privacy. What remains is server-side metadata describing the upload or post.
Social Media Platforms and Metadata Handling
Social media platforms have specific ways of handling both image and video metadata:
- Facebook and Instagram: Strip most EXIF data, retaining only certain fields related to rights, such as Creator and Copyright Notice, while removing GPS data and other sensitive information.
- Twitter: Retains minimal EXIF data, focusing on technical details like the camera model, while stripping GPS data.
- Pinterest: Removes GPS data and focuses on retaining technical details.
- Flickr: Unlike other platforms, Flickr preserves most of the EXIF data, making it a valuable resource for photographers [2].
Instead of preserving EXIF data, social media platforms generate their own server-side metadata, which typically includes:
- Upload Timestamp: When the file was added to the platform.
- User Information: Details about the user who uploaded the file.
- Post/Page Identifiers: Links to the page or user profile.
- Location Tags: If manually added during the post [3].
This server-generated metadata is an artifact of the platform's system, excluding original client-side data like EXIF. It reflects actions on the platform and can be admissible in court as evidence of user activity.
Legal and Investigative Implications
Misinterpretation of metadata can have significant legal implications. For instance, a timestamp in HTML metadata might be incorrectly attributed to the original file's capture time, rather than when it was uploaded. This confusion could lead to overstating or mischaracterizing the nature of the metadata in a legal context [3].
Several legal cases highlight the importance of correct metadata interpretation:
- In SPV-LS, LLC v. Transamerica Life Ins. Co., metadata revealed that an agreement, purportedly signed on a specific date, was actually created nearly a year later, negating a party's argument [3].
- North American Medical Corp. v. Axiom Worldwide, Inc. demonstrated how metadata could be used to prove trademark infringement through website optimization techniques [3].
- United States v. Goldstein showcased the relevance of cell site location information (CSLI) as metadata in tracking an individual's movements [4].
These cases underscore the critical role of metadata in establishing the authenticity and credibility of digital evidence.
Practical Advice for Investigators
To effectively utilize metadata in investigations, consider the following:
- Understand the Types of Metadata: Clearly differentiate between HTML metadata, EXIF data, and video metadata, and recognize their respective roles in digital forensics [5].
- Use Appropriate Tools: Employ tools designed to extract and analyze the right type of metadata. Some recommended tools include:
- Document Metadata Properly: Ensure that metadata is documented and contextualized correctly for court use. Maintain a clear chain of custody to preserve the metadata's authenticity and admissibility [8].
- Be Aware of Platform-Specific Handling: Understand how different social media platforms handle metadata, particularly the stripping of EXIF data and generation of server-side metadata [9].
- Stay Informed on Legal Standards: Be aware of the legal standards and ethical considerations when handling metadata, especially in relation to privacy and data protection laws [10].
Conclusion
Understanding the differences between HTML metadata and EXIF data is crucial for digital forensic investigators and legal professionals. Each type of metadata serves a unique purpose and provides different insights into digital evidence. By accurately interpreting these data types, investigators can enhance the reliability of their findings and support legal cases effectively. As the digital landscape continues to evolve, staying informed about metadata handling practices, especially on social media platforms, is essential. This knowledge ensures that investigators can navigate the complexities of digital evidence, maintaining its integrity and maximizing its value in legal proceedings.
References
[1] CaseGuard, "Digital Evidence: EXIF Data," 2024. [Online]. Available: https://caseguard.com/articles/digital-evidence-exif-data/
[2] Ironhack, "Metadata Forensics: When Files Can Speak and Reveal the Truth," 2024. [Online]. Available: https://www.ironhack.com/us/blog/metadata-forensics-when-files-can-speak-and-reveal-the-truth
[3] J. Smith, "The Litigation of Metadata – Your Devices Are Watching You," JD Supra, Jan. 15, 2024. [Online]. Available: https://www.jdsupra.com/legalnews/the-litigation-of-metadata-your-devices-7652639/
[4] International Research Journal of Law and Political Sciences, "Problems of Admissibility and Reliability of Metadata," vol. 15, no. 2, pp. 45-67, Mar. 2024. [Online]. Available: https://irshadjournals.com/index.php/ijlp/article/download/208/174/599
[5] First Monday, "The Use and Impact of Metadata in Digital Forensics," vol. 29, no. 1, Jan. 2024. [Online]. Available: https://firstmonday.org/ojs/index.php/fm/article/view/11605/10191
[6] Neotas, "OSINT Sources and Social Media Intelligence," Technical Report, Feb. 2024. [Online]. Available: https://www.neotas.com/osint-sources-social-media-osint/
[7] CyberTalents, "Cyber Crime Investigation Guide," White Paper, Mar. 2024. [Online]. Available: https://cybertalents.com/blog/cyber-crime-investigation
[8] Hackernoon, "Revealing the Digital Detective: Essential OSINT Tools and Techniques," Blog Post, Feb. 2024. [Online]. Available: https://hackernoon.com/revealing-the-digital-detective-essential-osint-tools-and-techniques-for-investigators
[9] National Institute of Standards and Technology, "Guide to Integrating Forensic Techniques into Incident Response," NIST Special Publication 800-86, Dec. 2023. [Online]. Available: https://www.nist.gov/publications/guide-integrating-forensic-techniques-incident-response
[10] Scientific Working Group on Digital Evidence (SWGDE), "Best Practices for Digital Evidence Collection," SWGDE Document v4.0, Jan. 2024. [Online]. Available: https://www.swgde.org/documents/published
[11] K. G. Hartman, "EXIF Might Matter: Demystifying Photo Metadata," Lucid Truth Technologies, Dec. 2024. [Online]. Available: https://lucidtruthtechnologies.com/photo-metadata/