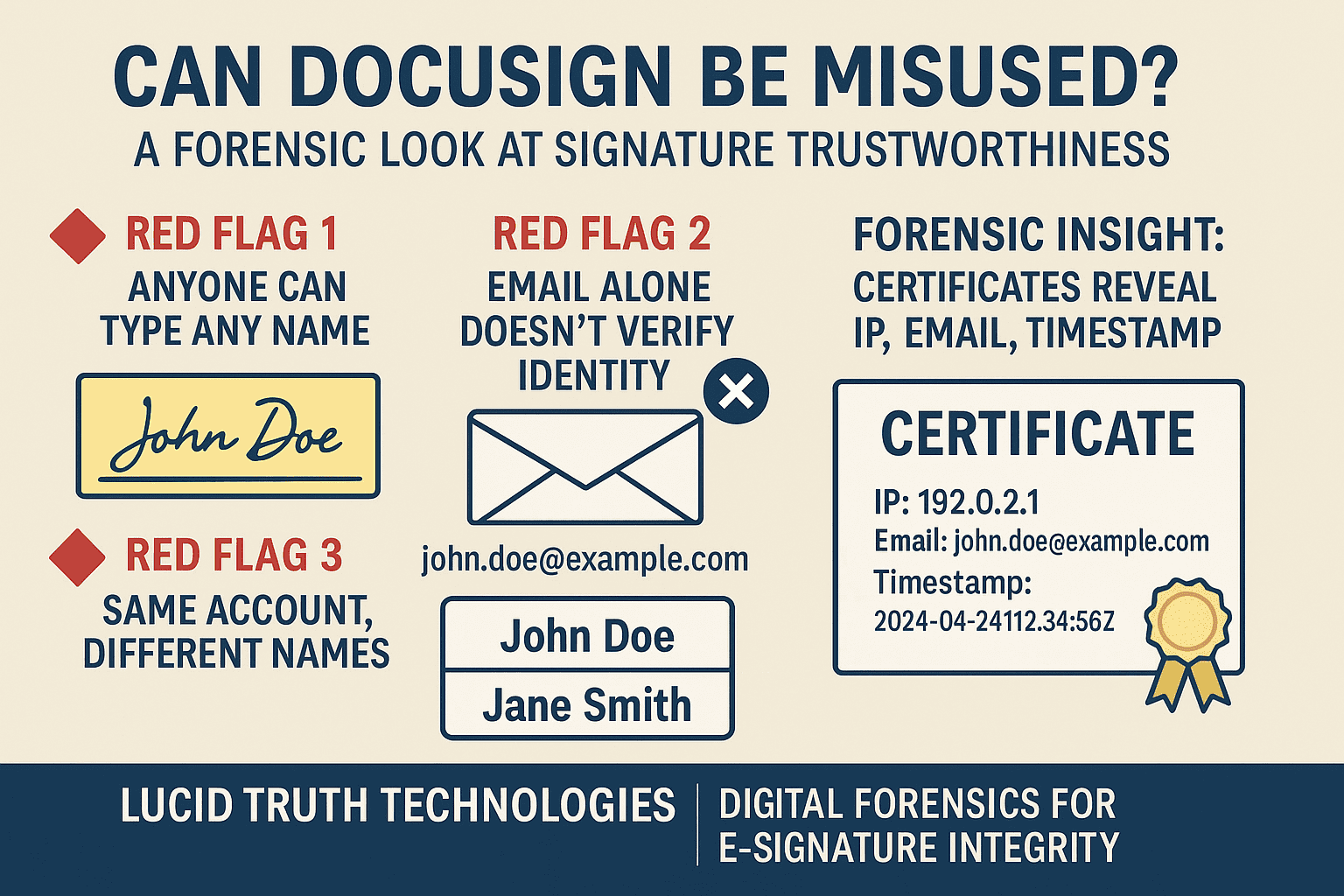
When a case hinges on a sliver of digital evidence—often just an IP address—it’s tempting to treat that data point as a smoking gun. But in the world of digital forensics, IP addresses behave more like fingerprints left on a public railing: possibly significant, often misleading, and always in need of proper context.
This post walks criminal defense attorneys and professional investigators through the complexities of IP address evidence in criminal investigations. Whether you're defending a client accused of cybercrime or tracing a digital trail in a private case, understanding what IP data really reveals can be the difference between a breakthrough and a blind alley.
1. IP Addresses: A Digital Breadcrumb, Not a Person
An IP address simply identifies a device on a network. In IPv4 format, it looks like 192.0.2.1; in IPv6, it’s a longer hexadecimal string like 2001:db8::ff00:42:8329. These addresses are typically assigned dynamically via DHCP or, in fewer cases, statically by a network administrator.
Think of an IP address like a return address on an envelope—useful, but not authoritative. Just because a client’s name appears on the label doesn’t mean they wrote the letter.
2. Dynamic IPs and Residential Network Pitfalls
Most residential internet users receive dynamic IP addresses through DHCP leases from their internet service provider. These leases expire and renew periodically, meaning the same IP may rotate between devices or users. Even slight discrepancies in lease timing or log synchronization can compromise attribution.
Residential networks often lack control and recordkeeping:
- Neighbors may use unsecured Wi-Fi
- Guests can connect using a well-known shared password
- Consumer routers do not generate logs by default
- Smart home devices constantly generate background traffic
When evaluating digital evidence, ask: Who had access to this network at the time of the alleged activity?
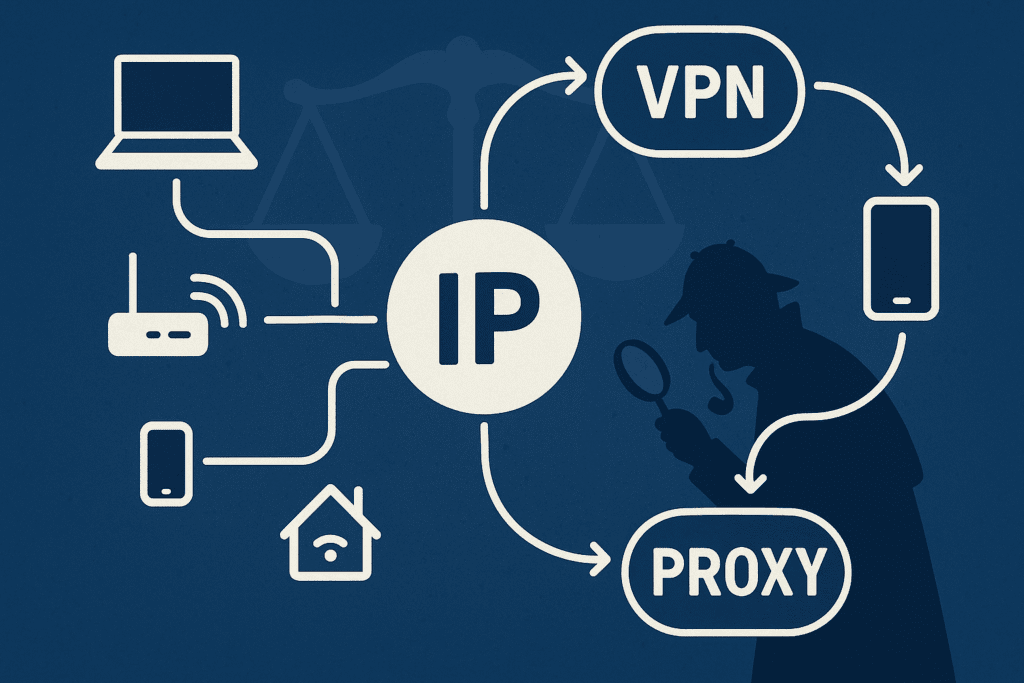
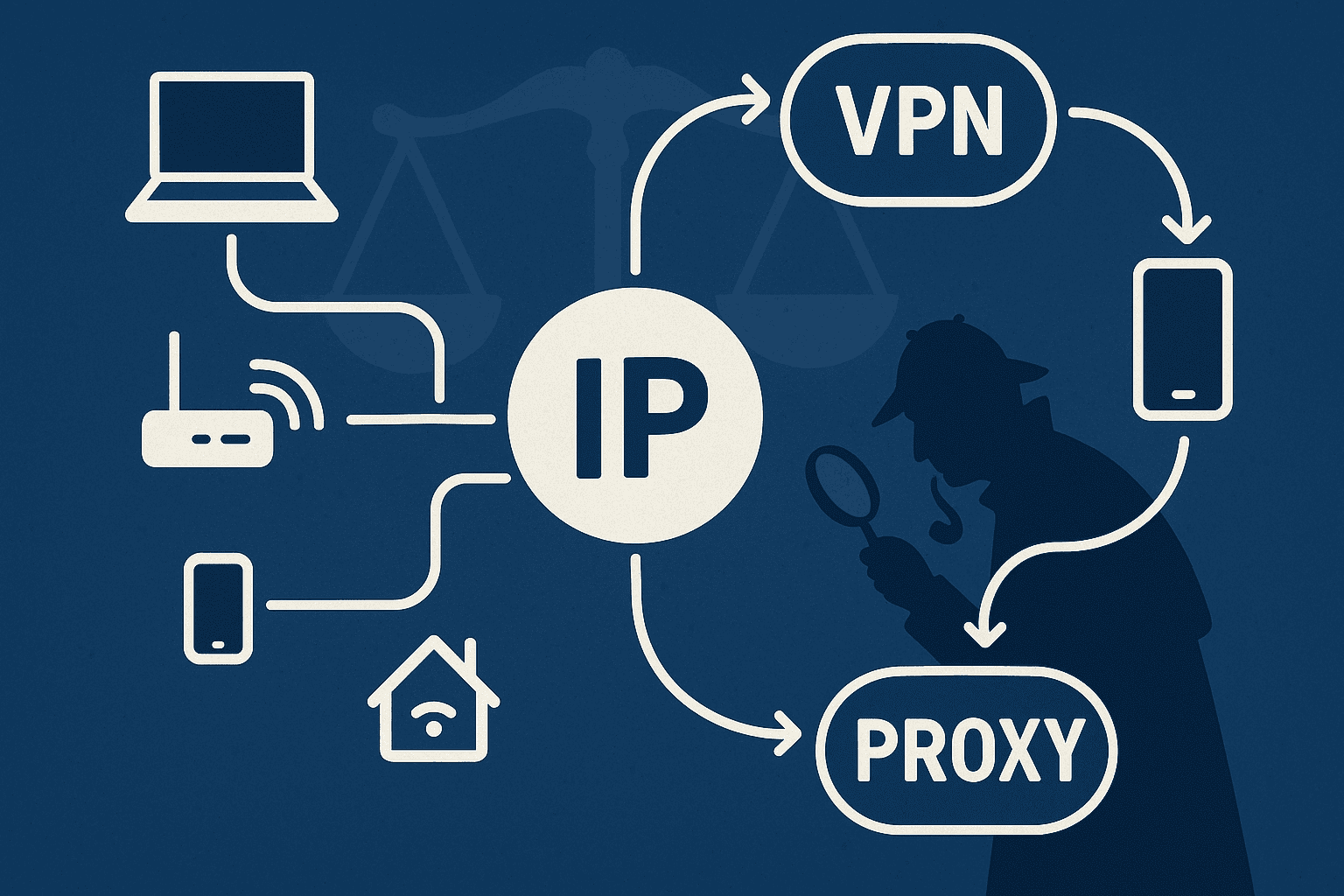
3. VPNs, Proxies, and Location Misdirection
Many users—casual and advanced—regularly disguise their IP addresses using:
These technologies route traffic through remote servers, making geolocation unreliable. That Romanian IP might simply be a VPN exit node shared by thousands.
Still, investigators can subpoena session logs from VPN providers—if those providers retain logs. However, privacy-focused services often advertise “no logs” policies, limiting access to such records.
Understanding the role of VPNs is essential when assessing IP address evidence in criminal investigations. Investigators and attorneys must evaluate whether traffic originated from a traceable source or a privacy tool.
4. Use IP Reputation Data with Caution
Reputation databases such as Spamhaus or Cisco Talos provide insight into whether an IP address has been linked to malicious behavior. But this data is:
- Frequently updated or removed
- Often shared across users, especially with VPNs.
- Not reliable for attribution in court
While this kind of digital evidence helps build context, it should never serve as the sole basis for legal conclusions. Criminal defense attorneys must scrutinize whether reputation data has been misapplied. Also note that IP addresses associated with VPN exit nodes will typically have a low reputation because VPN technologies are used to hide the illegal behavior of the VPN provider's other customers.
5. IP Spoofing Isn’t a Catch-All Defense
IP spoofing involves forging the source address in a packet header. While this tactic can succeed in stateless protocols like UDP, it fails in TCP connections, which require a three-way handshake. Any return traffic gets routed to the spoofed IP, where it's discarded—because the system receiving it never initiated the communication.
So when someone claims, “The attacker spoofed their IP to frame my client,” make sure the evidence supports that scenario. IP spoofing won’t explain authenticated web sessions, email transmissions, or file uploads.
6. The Limits of Geolocation
IP-based geolocation tools (e.g., MaxMind, IP2Location) estimate location based on ASN and ISP data. However, accuracy varies:
- City-level resolution is unreliable
- Mobile networks and carrier-grade NAT obscure exact locations
- VPNs distort actual geography
Geolocation may be sufficient for determining jurisdiction or justifying a search warrant, but it rarely holds up as standalone evidence. Lawyers should demand corroboration—device logs, account activity, or physical evidence.
7. ASN and IP Block Analysis
Every IP address belongs to an Autonomous System Number (ASN)—an organization like an ISP, university, or enterprise managing a block of IPs. WHOIS records help determine:
- Who owns the IP block
- Whether the address points to a residential user or a data center
- If multiple users share the same block
IP forensic analysis becomes more meaningful when contextualized with ASN data. Defense teams must ask whether investigators distinguished between commercial traffic and individual users.
8. IPv6: Emerging, But Underutilized
While IPv4 remains dominant, IPv6 is growing rapidly. It offers:
- Vastly larger address space
- More stable device assignments
- Enhanced traceability under some conditions
However, privacy extensions can mask device identifiers, and many forensic tools still lag in IPv6 support. Digital evidence involving IPv6 must be scrutinized for both its attribution value and its privacy implications.
9. Essential Questions to Ask About IP Evidence
When presented with IP address evidence in criminal investigations, ask:
- What time and date was the IP recorded?
- Was it assigned dynamically, and what was the lease duration?
- How accurate was the geolocation method used?
- Does the service provider retain logs, and were they preserved?
- Could the IP belong to a VPN exit node, proxy, or shared network?
- What additional data links the IP to a person or device?
Remember: an IP address is a starting point—not a conclusion.
Conclusion: Treat IP Data as Clue, Not Confirmation
IP address evidence in criminal investigations plays a vital role—but it must be treated with skepticism and contextual understanding. Legal teams and investigators should challenge assumptions, dig deeper into supporting data, and avoid over-reliance on this single data point.
Need expert support on IP forensic analysis or digital evidence review? Contact Lucid Truth Technologies for strategic consulting tailored to your case.