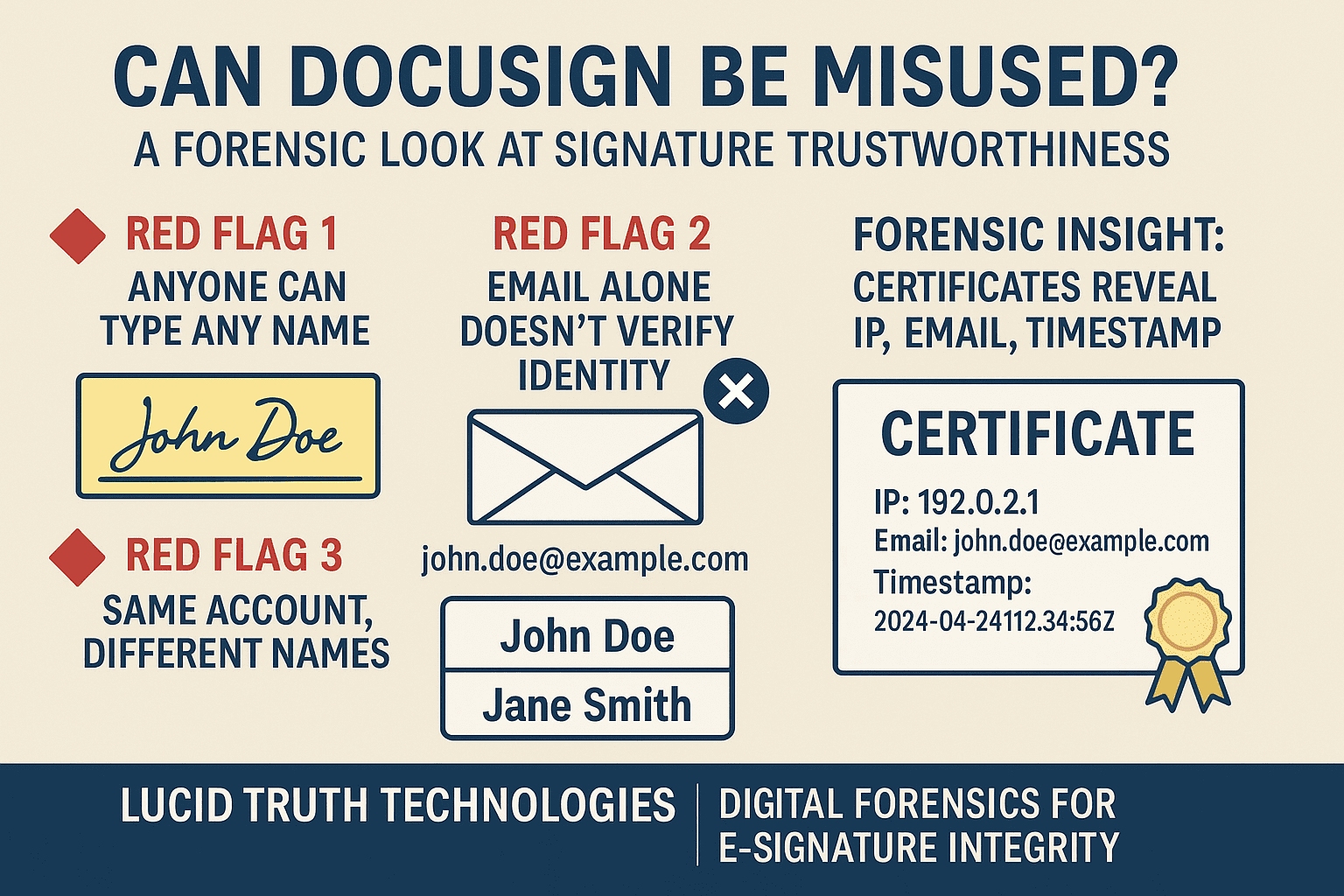
Electronic signatures offer convenience—but at what cost to security and authenticity? Our recent forensic investigation highlights critical weaknesses in common implementations of DocuSign’s basic electronic signature, especially when used without enhanced verification settings.
The Problem with Basic E-Signatures
DocuSign supports several types of electronic signatures, but the most widely used in the United States is the basic “Electronic Signature.” Unlike advanced or qualified signatures, this type does not require rigorous identity validation. Signers can enter any name, adopt any font, or even submit someone else’s name—without cryptographic binding to a verified identity.
Key Observation: A malicious user can impersonate another signer simply by entering their name and routing the document to an email address they control.
Email ≠ Identity
DocuSign does not require recipients to authenticate using an account tied to the signature. As a result:
- Non-subscribers can still execute documents.
- Email recipients can override the name associated with their signature.
- Multiple signatures using the same email address remain undetected unless a forensic expert investigates them.
Recommended Best Practice:
Always include the recipient’s email address directly on the signed document using DocuSign’s form fields to increase transparency and auditability.
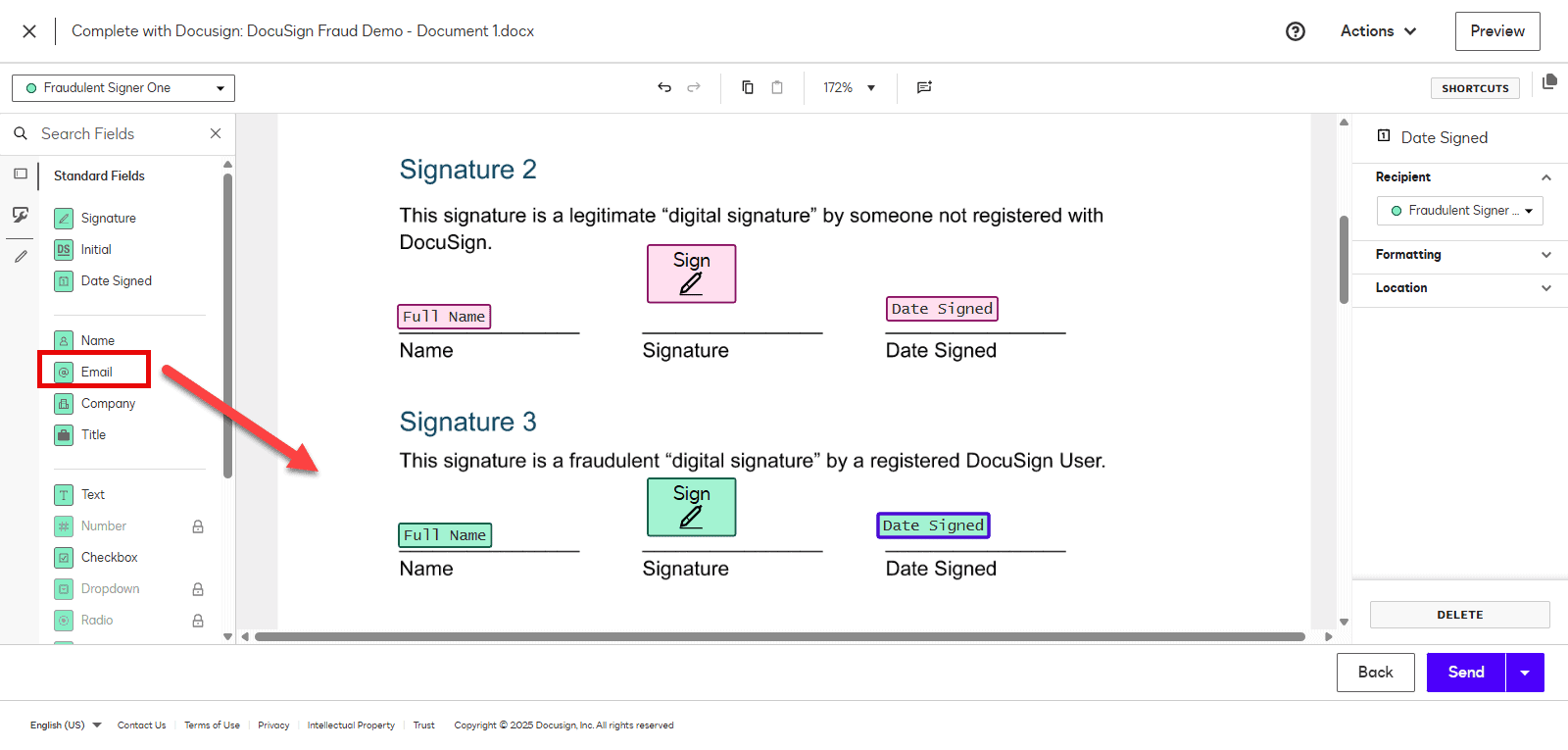
Figure 1: DocuSign form fields with colored recipient assignments, demonstrating how email fields can be added to increase document transparency and auditability.
Signature Customization Enables E-Signature Impersonation
Recipients have several ways to customize their signatures:
- Select from previously used signatures.
- Upload a scanned image of a signature.
- Draw or type a new signature using any chosen name.
This flexibility allows electronic signature abuse. Even though every signature includes a persistent DocuSign identifier, the average user rarely checks this identifier—making it easy to misuse and impersonate identities.
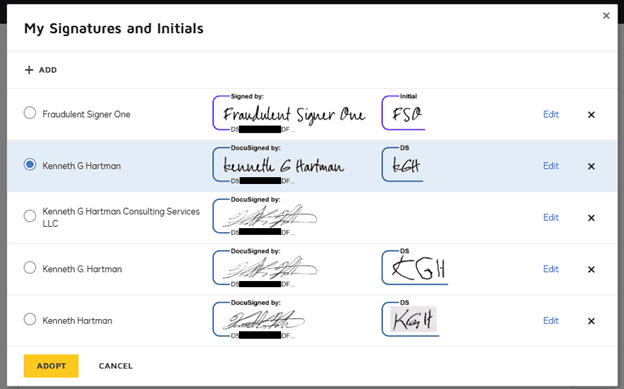
Figure 2: Multiple signatures linked to the same DocuSign account, demonstrating how names can vary while the underlying identifier remains constant.
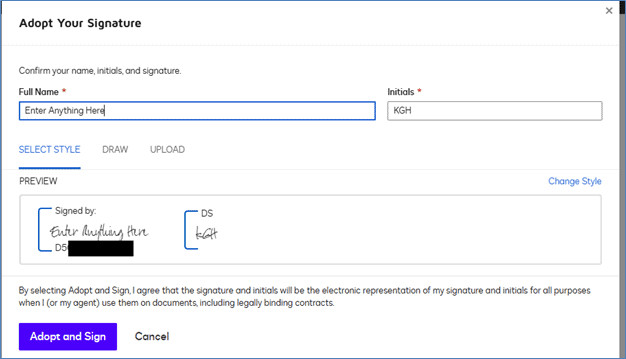
Figure 3: Demonstration of unverified identity claims, showing how users can enter arbitrary text like “Enter Anything Here” in the Full Name field.
Hidden in Plain Sight: The Certificate of Completion
One of the most powerful yet overlooked forensic artifacts is the Certificate of Completion. This report includes:
- Email addresses of signers
- IP addresses
- Timestamps
- Envelope metadata
Forensic analysts can use these data points to expose DocuSign forgery risks—such as detecting when two “different” signers originate from the same device/IP address or when the claimed identity doesn’t match the underlying metadata.
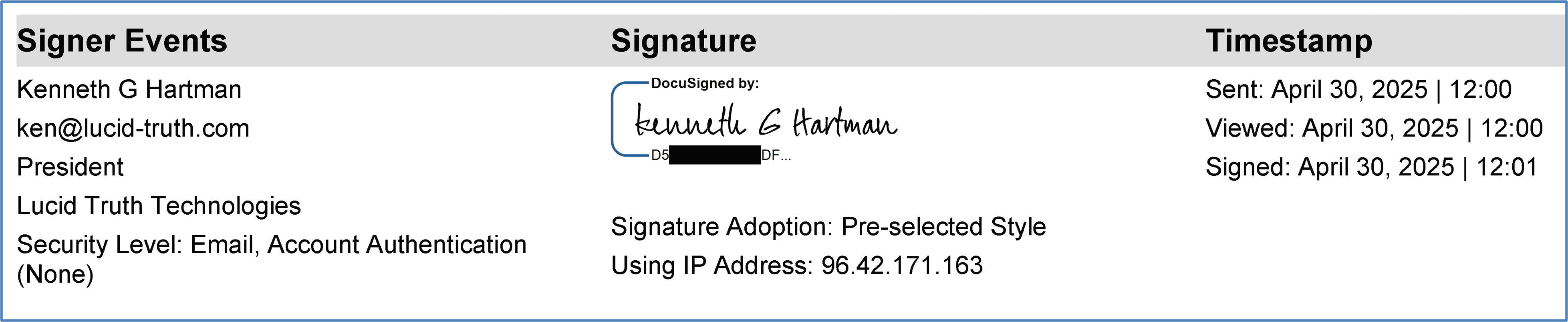
Figure 4: Legitimate signer metadata from the Certificate of Completion, showing identity information and associated account details.
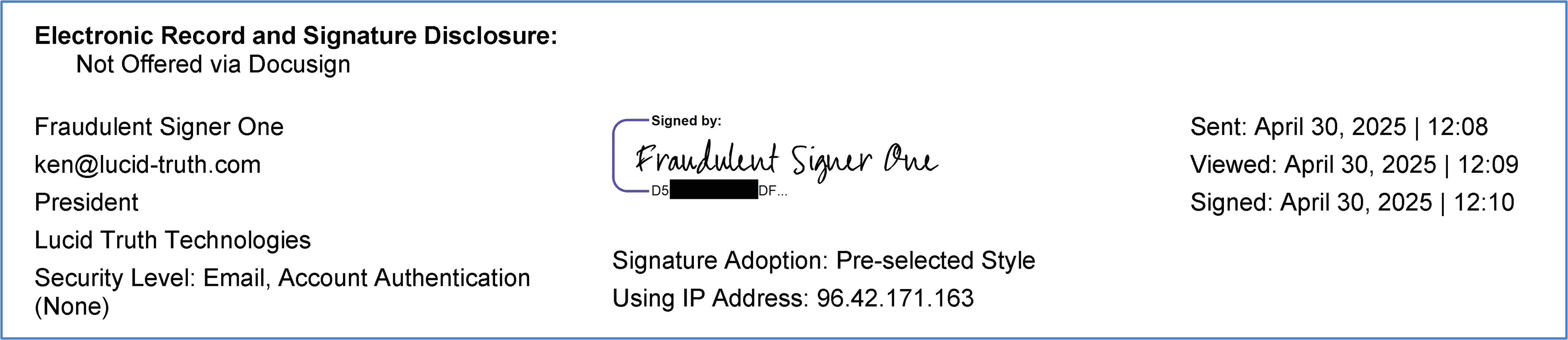
Figure 5: Forensic evidence of potential impersonation, showing the same DocuSign identifier being used with different names in the signature metadata.
Practical Takeaways
- Use advanced or qualified e-signatures when possible.
- Never rely solely on the name displayed—always request the Certificate of Completion with every signed document.
- Educate clients on electronic signature abuse and its legal implications.
- Include identifying fields (like email) visibly in signed documents.
- Watch for signs of DocuSign identity spoofing by examining metadata and signature consistency.
How Lucid Truth Technologies Can Help
Lucid Truth Technologies offers expert digital forensics services to evaluate the authenticity and provenance of electronically signed documents. Whether you’re challenging the integrity of a signature or need a defensible review of signing events, our team provides unbiased, technically sound, and court-admissible insight.
If you’re concerned about e-signature impersonation or electronic document fraud in your legal matter, contact us today to learn how we can help.