Digital Hashing for Lawyers: Understanding the Essentials for Criminal Defense
Introduction
In the digital age, where most of our communications, transactions, and even personal activities leave a digital footprint, understanding the nuances of digital forensics has become crucial for legal professionals, particularly criminal defense lawyers. One such nuance, often overlooked yet fundamental in the realm of digital evidence, is 'digital hashing'. This term might sound technical and intimidating at first, but its concept is straightforward and its implications in legal proceedings are profound.
Digital hashing is a process that transforms an arbitrary block of data (like an email, a photograph, or a document) into a unique fixed-size string of characters, known as a hash. This hash functions almost like a digital fingerprint; uniquely identifying its corresponding data. In the legal context, hashing is not just about technology; it's about integrity, authenticity, and the unimpeachable chain of custody of digital evidence.
As a criminal defense lawyer, understanding hashing is not about becoming a tech expert, but about grasping how this digital process can impact the evidence presented in your cases. Whether it's challenging the authenticity of a piece of digital evidence or understanding the testimony of a digital forensic expert, a basic understanding of digital hashing can be a game-changer in your practice. This article aims to demystify digital hashing and highlight its significance in the legal field, providing you with the knowledge needed to navigate the increasingly digital landscape of criminal defense.
What is Digital Hashing?
At its core, digital hashing is a cornerstone of computer science, but its implications extend far into the realm of criminal defense law. To grasp its significance, it's essential to understand what hashing is and how it functions.
The Basics of Hashing
Hashing is a process that converts an input (or 'message') into a fixed-size string of bytes. The output, known as a hash, is typically a short string representative of the original data. Think of it like a culinary recipe turning a specific set of ingredients into a distinct dish. No matter where or how many times you prepare the recipe, the same ingredients will always yield the same dish. Similarly, a particular piece of data, when passed through a hash function, always produces the same hash.
Uniqueness and Consistency
The most crucial aspect of hashing is its ability to produce a unique output for every unique input. Just as no two people have the same fingerprint, no two different pieces of data should produce the same hash. This uniqueness is pivotal in legal contexts, particularly for verifying the integrity of digital evidence. If even a single character in a document is altered, the hash will change drastically – a property known as the "avalanche effect".
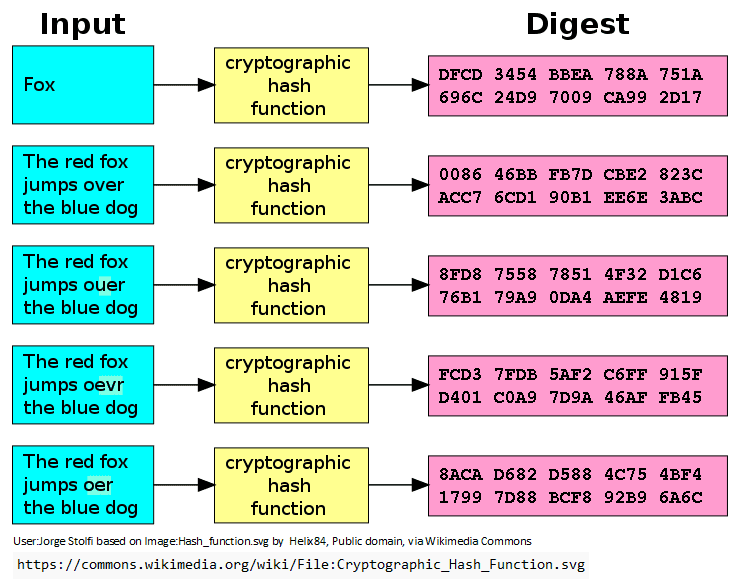
In short, digital hashing acts like a digital seal. It is an invaluable tool in the arsenal of criminal defense lawyers, offering a reliable method to validate the integrity of digital evidence. As digital data becomes increasingly prevalent in legal cases, the understanding and application of digital hashing becomes not just useful but essential for effective legal defense.
The Role of Hashing in Digital Forensics
In the realm of digital forensics, hashing plays a pivotal role. It's a tool that lawyers, especially those in criminal defense, need to understand to effectively navigate the complexities of digital evidence. This section delves into the practical application of hashing in digital forensics and its significance in legal investigations.
Ensuring Authenticity of Digital Evidence
The primary role of hashing in digital forensics is to ensure the authenticity of digital evidence. Authenticity, in this context, refers to the assurance that the evidence presented in court is the same as that collected during the investigation. When a digital file is hashed at the time of collection, it creates a digital 'fingerprint' of that file. Later, forensic experts can re-hash the file to verify that the 'fingerprint' remains unchanged, thereby ensuring the file's authenticity.
Detecting Tampering and Alterations
Hashing is a powerful tool in detecting any form of tampering with digital evidence. Given the sensitivity of digital data, where altering even a single bit can change the entire content, hashing acts as a gatekeeper. A mismatch between the original hash and a later hash of the same file is a clear indicator of alteration. This can be crucial in legal scenarios where the integrity of evidence can make or break a case.
Hashing in Cybercrime Investigations
With the rise of cybercrime, hashing has become an indispensable tool for investigators. For example, in cases involving malware, phishing, or unauthorized access, hashing helps in identifying and comparing known malicious software with suspected ones found during an investigation. It can also be used to verify the integrity of logs and records, which are often targeted in cybercrimes to erase traces of illegal activity.
Real-World Legal Cases Involving Hashing
Hashing has proven to be an invaluable tool in various legal contexts, especially in intellectual property theft and in combating child sexual abuse material (CSAM). The following real-world scenarios provide a glimpse into the practical applications and impact of hashing in legal investigations.
Intellectual Property Theft
In a case of intellectual property theft, a company accused a former employee of stealing confidential data. Forensic experts used hashing to match the hash values of files found on the ex-employee's devices with those of the confidential files. This process proved that the files were indeed copied and transferred, demonstrating the power of hashing in identifying unauthorized duplication and transmission of digital data.
Combating Child Sexual Abuse Material (CSAM)
The National Center for Missing and Exploited Children (NCMEC) utilizes hashing as a cornerstone technique in the fight against child sexual abuse material online. NCMEC maintains a database of hashes known as the Child Recognition and Identification System (CRIS). This database contains hashes of verified CSAM images and videos.
When a digital platform encounters potential CSAM, it can hash the content and compare the hash against those in the CRIS database. If there's a match, it indicates the presence of known CSAM. This method allows systems to rapidly identify and report such material without requiring individuals to view the content directly, thereby minimizing traumatic exposure.
Hashing also plays a crucial role in the legal proceedings against distributors of CSAM. The matched hashes serve as compelling evidence, linking suspects to the possession or distribution of known illegal material. This application of hashing underscores its importance as a tool not only for identification but also for legal accountability.
Challenges in the Use of Hashing
While hashing is a robust tool, it is not without its challenges. For instance, advanced techniques like cryptographic attacks can, in rare cases, produce the same hash from different data (known as a hash collision). Additionally, the process of hashing and the choice of hash function are crucial – using outdated or weak hash functions can lead to vulnerabilities.
Understanding the role of hashing in digital forensics is vital for criminal defense lawyers. It is a key to ensuring the integrity of digital evidence and plays a significant role in cases involving digital data. As digital evidence becomes more prevalent in legal cases, the knowledge of digital hashing and its applications in forensics will be increasingly important for effective legal practice.
Hashing and Chain of Custody
The integrity of evidence is a cornerstone of legal proceedings, and the digital realm is no exception. Hashing plays a crucial role in maintaining the chain of custody for digital evidence, proving that it remains untampered from the point of collection to its presentation in court.
The Chain of Custody in Digital Evidence
In legal terms, the chain of custody refers to the chronological documentation or paper trail that records the sequence of custody, control, transfer, analysis, and disposition of physical or electronic evidence [1]. It's vital in legal proceedings to establish the integrity and authenticity of evidence. For digital evidence, this process can be complex, given the ease with which digital data can be altered.
Role of Hashing in Maintaining Integrity
Hashing ensures that each step in the digital chain of custody is verifiable. When digital evidence is first collected, it is hashed to produce a unique digital fingerprint. This hash is then documented and preserved. At each subsequent point where the evidence is accessed or transferred, it is rehashed, and the new hash is compared with the original.
Case Example: Securing Digital Evidence
Consider a scenario where digital evidence from a corporate computer needs to be analyzed for a fraud investigation. The initial hash is taken when the evidence is collected. When the evidence reaches the forensic lab, it's hashed again before analysis. Post-analysis, before being submitted to court, the evidence is hashed a third time. At each point, the consistency of the hash values ensures the evidence remains unchanged, maintaining its integrity throughout the investigative process.
Hashing and Evidentiary Challenges
The use of hashing in maintaining the chain of custody also prepares defense attorneys to face and respond to evidentiary challenges. Understanding the hashing process enables them to question any discrepancies in the chain of custody and potentially challenge the admissibility of compromised digital evidence.
Collaborating with Digital Forensic Experts
In the intricate landscape of criminal defense, the complexity of digital evidence often necessitates the involvement of digital forensic experts. These specialists play a pivotal role in deciphering the technical intricacies of digital data, particularly in the context of hashing.
The Imperative for Expertise in Digital Forensics
Digital forensic experts are essential for their deep understanding of how digital evidence is retrieved, analyzed, and preserved. For criminal defense lawyers, hashing can seem like a daunting technical process, but forensic experts can provide critical insights and clarity.
Strengthening Legal Strategy Through Expert Collaboration
Collaborating with forensic experts allows lawyers to fortify their legal strategies. Experts can elucidate the specifics of how digital evidence, underpinned by hashing, was handled and processed. Such insights are invaluable for building a formidable defense, especially when the integrity of digital evidence is in question.
Effective Communication with Forensic Experts
A key element of this collaboration is effective communication. Lawyers should be prepared to ask forensic experts detailed questions about the hashing process, including the types of hash functions used, their reliability, and any potential vulnerabilities that might exist.
Case Study: Challenging Digital Evidence
Imagine a scenario where a defendant is implicated in a data breach incident based on digital logs. The prosecution claims these logs unequivocally link the defendant to the breach. A digital forensic expert, working with the defense, examines the hashing methodology used in securing these logs. The expert discovers that due to a flawed hashing process, the logs could have been compromised or manipulated post-incident. This revelation casts doubt on the reliability of the evidence and opens new avenues for the defense strategy, potentially altering the case's trajectory.
Keeping Up with Digital Forensic Trends
The field of digital forensics is evolving constantly, paralleling the advancements in technology. It is imperative for criminal defense lawyers to stay abreast of these developments. Regular interactions with forensic experts can equip lawyers with the latest techniques and knowledge in digital evidence handling.
Conclusion
As digital evidence becomes increasingly crucial in criminal cases, a fundamental understanding of digital hashing is essential for criminal defense lawyers. This knowledge not only aids in ensuring the integrity of evidence but also enhances the overall defense strategy in the digital realm.
Ultimately, the alliance between criminal defense lawyers and digital forensic experts (like Lucid Truth Technologies) is critical in the digital age. This collaboration empowers lawyers to effectively navigate the complexities of digital evidence, leveraging expert knowledge in hashing and other forensic methodologies to build a more informed and effective defense.
[1] Digital Forensic: The Chain of Custody | Andrea Fortuna. https://andreafortuna.org/2018/04/09/digital-forensic-the-chain-of-custody/